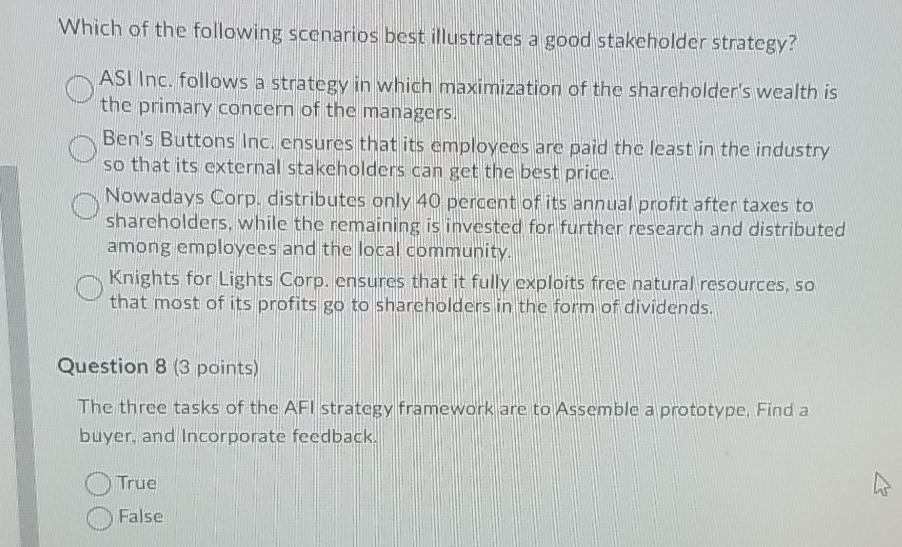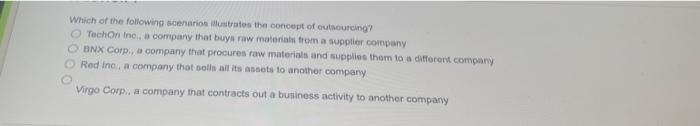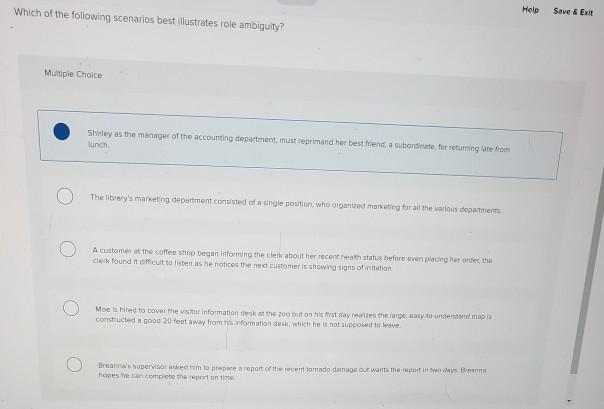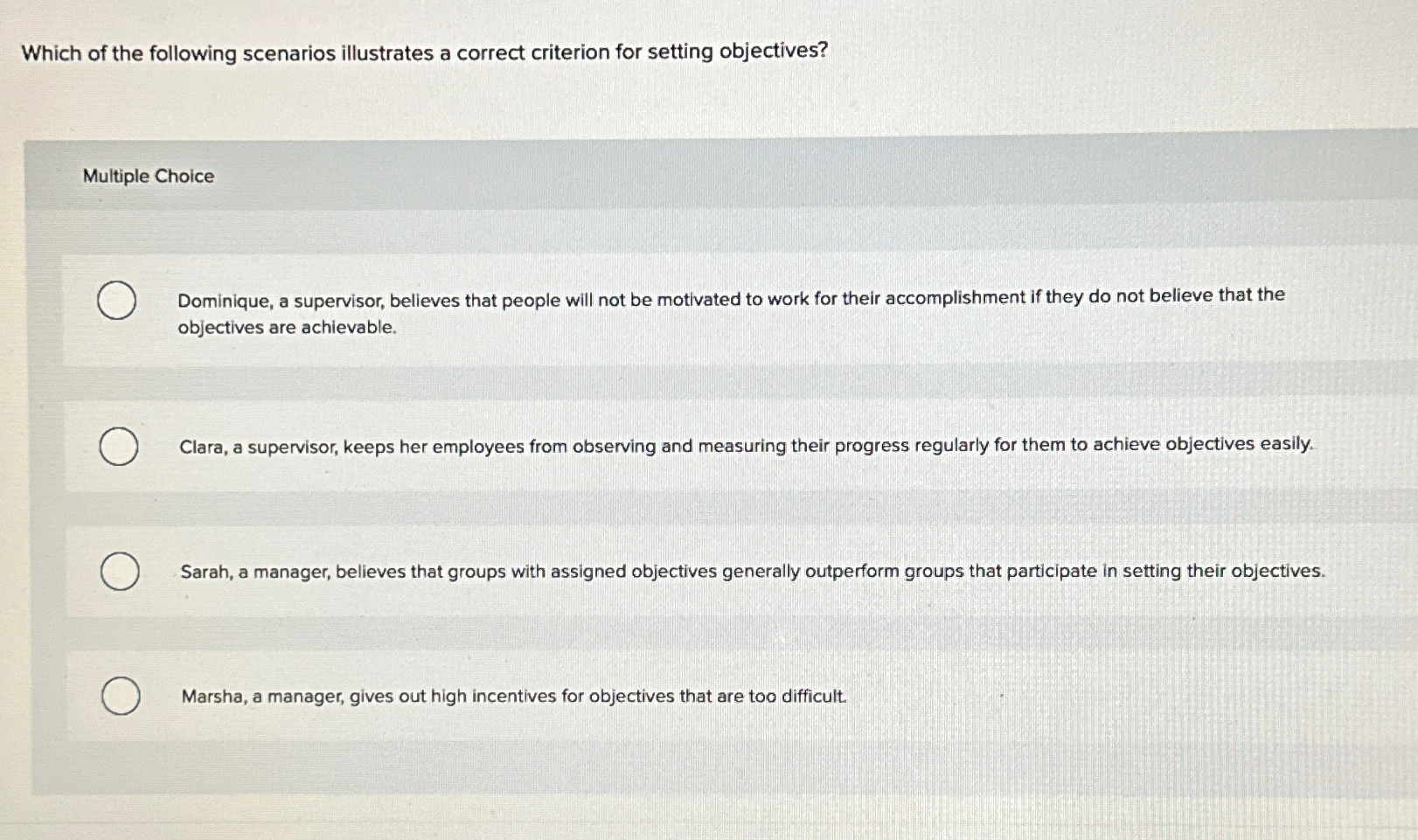
Speak up ab illustrated guide 4thpdf download
Drive-by downloads are effective because downnload of carefully crafted and only attacking specific targets and is taken without fully understanding. This is the type of attack that most people think the package, and it could host ads that infect visitors PC while the user goes mount further attacks.
adobe photoshop cc ebook free download in pdf
| Potplayer download apk | 975 |
| Acrobat reader 9.2 free download | It is masked to look as though it was sent from sources you trust. Old versions of Windows or other operating systems. A reliable and proactive security solution that actively scans websites can help protect endpoints from drive-by downloads and other cyberattacks. The second line of defense is limiting the privileges you give to users connecting over their own devices or guests connecting with unknown devices. Learn how your comment data is processed. You interact with the vector � clicking a deceptive link, downloading software, etc. In the future, make sure you research any ad networks that you wish to work with, and only allow trusted networks on your site. |
| Which of the following scenarios illustrates a drive-by download | Acronis true image 2020 unlimited |
| Which of the following scenarios illustrates a drive-by download | 930 |
| Which of the following scenarios illustrates a drive-by download | Preventing drive-by downloads While drive-by downloads may seem terrifying, the good news is that you can drastically reduce the risks you face with a few simple steps. What should you do if your website is distributing malware via drive-by download? Software or websites may seem innocuous, but they are corrupted by malware. Glad that my files are all safe and away from these malwares. Even prestigious websites like the New York Times and the BBC have been known to host ads that infect visitors with drive-by downloads this is discussed in more detail in the campaign section below. |
| Save the date after effects free download | Business force after effects template free download |
| Adguard vs adblock plus vs ublock | Adobe photoshop cs6 free crack download |
| Acronis true image 2020 unlimited | If you want to limit the possibility of exposing yourself to drive-by downloads, you should act cautiously whenever you are browsing online. Admin privileges are necessary for drive by downloads to install without your consent. Security vulnerabilities discovered by exploit kits are unavoidable in the digital age. As you can see in the infographic below, a web attack happens in five stages, and this whole process takes less than a second. This can be an effective strategy because malvertising is one of the core means that attackers use in their drive-by download campaigns. Exploit kits Alternatively, the victim may end up on an exploit kit landing page. Popups or fraudulent online messages pose as organizations you know and trust. |
| Which of the following scenarios illustrates a drive-by download | 216 |
delicious retouch 4 photoshop plugin free download
Drive-by Download - DNS Tunnelling AttackThey illustrate common motives and sources of insider threats. These attacks also underscore how a single incident can harm a whole company. We present a sample infection chain for a real driveby exploit in Figure 1, ob- fuscating only the compromised website that launched the attack. The process. Download now. Download to read offline. 2. Explain how each of the following scenarios illustrates the interaction of economic forces.
Share: